In today’s volatile cybersecurity climate, businesses seem to be fighting a losing battle when it comes to defending against cyberattack. Organizations of all sizes are vulnerable to threats, incidents, and social engineering techniques—and when they don’t have the right defense systems in place, those threats and incidents often become a full-blown catastrophic data breach.

Today’s cyber criminal element is sophisticated, well funded, and persistent in its attack.
Ransomware and other elusive, human-dependent social engineering techniques make detection before infection tougher than ever. Ransomware can slip into a company system virtually undetected–until it’s too late. Once an unsuspecting employee accesses an infected file or email attachment and launches the ransomware Trojan, the resulting havoc can bring your business to a halt—and cause significant financial and reputational damage in the process.
Today’s cyber criminal element is sophisticated, well funded, and persistent in its attack. Even with strong antivirus protection, advanced firewalls, and continuous employee training, cyber criminals are still able to get around even the most advanced corporate perimeter defense systems. Hackers are exploiting businesses and their valuable data faster than most cybersecurity strategies can keep up.
With the recent spike in malware infections and ransomware attacks, companies are understandably rethinking their Disaster Recovery strategies.
The Risk Is Larger Than You Think
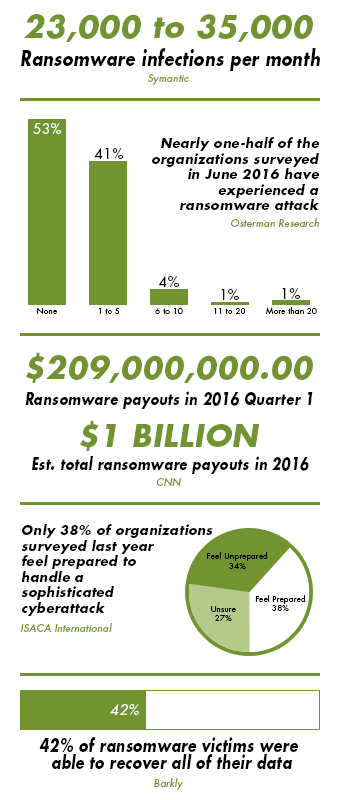 No organization is immune from the clever social engineering techniques deployed during a ransomware attack. In a recent survey, nearly one out of every two respondents reported at least one ransomware attack over the past year, and only 38 percent of global organizations feel prepared to handle a sophisticated cyberattack.
No organization is immune from the clever social engineering techniques deployed during a ransomware attack. In a recent survey, nearly one out of every two respondents reported at least one ransomware attack over the past year, and only 38 percent of global organizations feel prepared to handle a sophisticated cyberattack.
With 23,000 to 35,000 ransomware infections per month, the odds are stacked in the cyber criminal’s favor. Since cyber-extortion is nearing $209 million in ransomware payouts for the first part of 2016 alone, hackers are looking at a $1 billion ransomware profit this year—making it a favorite method of attack for the most opportunistic, relentless cyber criminal element.
All it takes is one employee clicking on one apparently harmless email attachment—and ransomware is unleashed on your organization’s systems, locking down valuable company files until the ransom is paid.
Unfortunately, even after a company pays the ransom, it isn’t guaranteed to get its files back. Sometimes, the cyber criminals simply refuse to unlock company files—as was the case with Kansas Heart Hospital, which paid the first ransom only to discover that its attackers would then demand a second payout. More often, less than half of all ransomware victims fully recover their data due to out-of-date, untested backups and the increased risk of ransomware infecting the onsite backups as well.
Cybersecurity Considerations in Disaster Recovery Planning
In the face of what seems to be a daily, unrelenting attack on business, organizations should ensure they have the proper cybersecurity safeguards and Disaster Response planning in place to prevent a critical situation from spiraling into a catastrophic event.
It’s important to try to learn from any threats and incidents that do occur, and plan for the reality that in today’s climate, it is likely another incident will occur in the future. Consider the following points when developing your organization’s cybersecurity strategy:
| 1 | What steps can your organization take to prevent threats and incidents from becoming a full-blown catastrophic data breach? |
| 2 | How can your organization identify threats and contain them before they become incidents? |
| 3 | How can your organization mitigate damages and recover as quickly as possible when a damaging event does occur? |
One of the most important cybersecurity precautions you can take involves having a sophisticated backup both onsite and offsite. Onsite backups should be safeguarded against the potential for compromise—especially in the event of a ransomware attack. Since most advanced ransomware  Trojans target onsite backup as part of their method of attack, a comprehensive offsite backup is good business practice and essential for total protection.
Trojans target onsite backup as part of their method of attack, a comprehensive offsite backup is good business practice and essential for total protection.
With the costs associated with a physical offsite backup location proving prohibitive for many small and medium-sized businesses, many organizations are adopting a cloud storage strategy as their means of safely backing up data offsite.
Regardless of where you choose to store your backup data, best practices dictate certain retention policies be established to keep data for a period that allows for recovery point objectives to be met, along with regular testing for the worst case scenario, keeping in mind total recovery time for business continuity purposes.
Comprehensive Disaster Response Planning is Necessary to Survive a Cyber Attack
We are entering a new era where ransomware and other malware variants are becoming more sophisticated than ever before. Organizations of all sizes should prepare in advance to ensure proper cybersecurity measures are in place before disaster strikes. For the ultimate business protection, companies should prepare for the inevitable cybersecurity incident with comprehensive disaster response and business continuity planning in order to stay up-and-running and recover quickly in a post-disaster environment.
By planning effectively for the worst case scenario—including breaches of current security measures, human error, and onsite backup compromise—you can protect your organization from becoming totally disabled during a cybersecurity event. By utilizing an offsite cloud DRaaS platform to manage your disaster response implementation and testing, you’ll always know your organization’s overall disaster response and cyber resiliency status. With SCC, your DRaaS expert will design a cost-effective, flexible, scalable solution tailored to your business’s unique needs to keep your business up-and-running and with minimal downtime during and after a disaster.















Leave a Reply
Want to join the discussion?Feel free to contribute!